The questions and answers to what it covers.
Today every Business, Healthcare Provider, Non-Profit & Municipal; Large or Small needs Cyber Liability Insurance. This is because the hacking activity is increasing each year; not only on large companies but also on smaller business. Verizon reported that approximately 40% of all data breaches last year occurred among companies with fewer than 100 employees.
Jim Lyons Insurance Agency writes for most major cyber liability insurance companies. This is because some may have a better rate for a select class of business that is better than other companies.
What is Cyber Liability Insurance?
The term “Cyber” implies coverage only for incidents that involve electronic hacking or online activities, when in fact this product is much broader, covering private data and communications in many different formats – paper, digital or even the lost laptop.
“Cyber” Liability is insurance coverage specifically designed to protect a business or organization from:
1. Liability claims involving the unauthorized release of information for which the organization has a legal obligation to keep private.
2. Liability claims alleging personal injury and/or intellectual property violations in a digital, online or social media environment.
3. Liability claims alleging failures of computer security that result in deletion/alteration of data, the transmission of malicious code, denial of service, etc.
4. Defense costs in State or Federal regulatory proceedings that involve violations of privacy law;
5. The provision of expert resources and monetary reimbursement to the Insured for the out-of-pocket (1st Party) expenses associated with the appropriate handling of the types of incidents listed above.
What does Privacy Liability cover?
The Security Liability insuring agreement provides coverage for the Insured for allegations of a “Security Wrongful Act”, including:
• The inability of a third-party, who is authorized to do so, to gain access to the Insured’s computer systems.
• The failure to prevent unauthorized access to or use of a computer system, and/or the failure to prevent false communications such as “phishing” that results in corruption, deletion of or damage to electronic data, theft of data and denial of service attacks against websites or computer systems of a third party.
• Protects against liability associated with the Insured’s failure to prevent transmission of malicious code from their computer system to a third party’s computer system.
What does Multimedia Liability cover?
The Multimedia Liability insuring agreement provides coverage against allegations that include: Defamation, libel, slander, emotional distress, invasion of the right to privacy, copyright and other forms of intellectual property infringement (patent excluded) in the course of the Insured’s communication of media content in electronic (website, social media, etc.) or non-electronic forms. Some “Cyber” insurance policies often limit this coverage to content posted to the Insured’s website. Our policy extends what types of media are covered as well as the formats where this information resides.
What does Cyber Extortion cover?
The Cyber Extortion insuring agreement provides: Expense and payments to a harmful third party to avert potential damage threatened against the Insured such as the introduction of malicious code, system interruption, data corruption or destruction or dissemination of personal or confidential corporate information.
What does Business Income and Digital Asset Restoration cover?
The Business Income and Digital Asset Restoration insuring agreement provides for lost earnings and expenses incurred because of a security compromise that leads to the failure or disruption of a computer system, or, an authorized third-party’s inability to access a computer system. Restoration costs to restore or recreate digital (not hardware) assets to their pre-loss state are provided for as well. What’s more, the definition of Computer System is broadened to include not only systems under the Insured’s direct control but also systems under the control of a Service Provider with whom the Insured contracts to hold or process their digital assets.
What is “PCI-DSS Assessment” coverage?
The Payment Card Industry Data Security Standard (PCI-DSS) was established in 2006 through a collaboration of the major credit card brands as a means of bringing standardized security best practices for the secure processing of credit card transactions. Merchants and service providers must adhere to certain goals and requirements in order to be “PCI Compliant,” and under specific agreements, may subject an Insured to an “assessment” for breach of such terms. Many Cyber and Privacy Liability Policy responds to PCI assessments as well as claims expenses in the wake of a breach involving cardholder information.
What is Cyber Deception coverage?
The Cyber Deception extension, if the applicant is eligible and if purchased for an additional premium, provides coverage for the intentional misleading of the Applicant by means of a dishonest misrepresentation of a material fact contained or conveyed within an electronic or telephonic communication(s) and which is relied upon by the Applicant believing it to be genuine. This is commonly known as “spear-phishing” or “social engineering”.
How is this policy better than other options in the marketplace?
As with any insurance policy, what sets our coverage apart lies in the definitions and exclusions in the policy. Some Cyber and Privacy Liability Policy offers comprehensive critical terms such as Privacy Breach, Computer System, and Media Content. These definitions, along with the absence of some industry standard exclusions and a drastically streamlined application process, make this policy more comprehensive and easier to access than the typical cyber policy available from traditional sources.
Is this already covered under most business insurance plans?
The short answer is “No”. While liability coverage for data breach and privacy claims has been found in limited instances through General Liability, Commercial Crime, and some D&O policies, these forms were not intended to respond to the modern threats posed in today’s 24/7 information environment. Where coverage has been afforded in the past, carriers (and the ISO) are taking great measures to include exclusionary language in form updates that make clear their intentions of not covering these threats. Additionally, even if coverage can be found in rare instances through other policies, they lack the expert resources and critical 1st Party coverages that help mitigate the financial, operational and reputational damages a data breach can inflict on an organization.
Many companies are now adding cyber liability coverage to business policies. The coverage is usually lower limits and coverage that is not as broad as standalone policies.
Are businesses required to carry this coverage?
While there is presently no law that requires a business or organization to carry Cyber Liability, there is a national trend in business contracts for proof of this coverage. In addition, the SEC is encouraging disclosure of this coverage as a way of demonstrating sound information security risk management. Laws such as HIPAA-HITECH and Gramm-Leach-Bliley and state-specific data breach laws are continually driving demand as requirements for notification in the wake of a data breach become more expensive.
Do small businesses need this coverage?
Small businesses accounted for 30% -40% of targeted spear-phishing attacks. Even more alarming is the fact that 60% of companies that have been a victim of cyber-attacks are out of business within six months. While breaches involving public corporations and government entities garner the vast majority of headlines, it is the small business that can be most at risk. With lower information security budgets, limited personnel and greater system vulnerabilities, small businesses are increasingly at risk for a data breach.
If e-commerce functions such as payment processing or data storage are outsourced, is this coverage still needed?
The responsibility to notify customers of a data breach or legal liabilities associated with protecting customer data, remain the responsibility of the Insured. Generally speaking, business relationships exist between Insureds and their customers, not their customers and the back-office vendors the Insured use to assist them in their operations. Outsourcing business-critical functions such as payment processing, data storage, website hosting, etc. can help insulate Insureds from risk. However, the contractual agreement wording between Insureds, their customers and the vendors with whom they do business will govern the extent to which liability is assigned in specific incidents.
What is the cost of not buying the coverage and self-insuring a data breach?
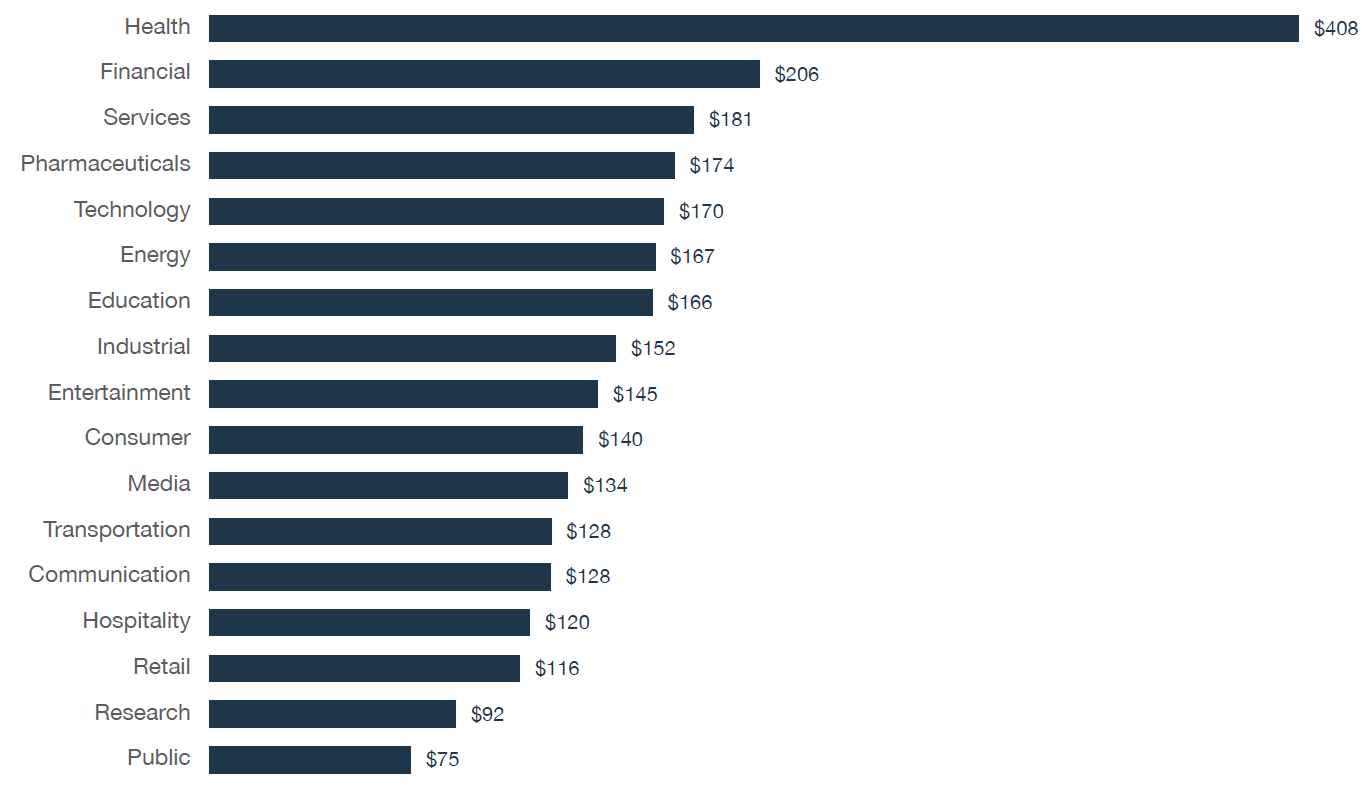
IBM and the Ponemon Institute publishes an annual “Cost of a Data Breach” report image below.. The 2018 report indicated that the average cost paid for each lost or stolen record is $141. Healthcare costs are much higher, with an average of $408 per record. These numbers are reflective of both the indirect expenses associated with a breach (time, effort and other organizational resources spent during the data breach resolution, customer churn, etc.), as well as direct expenses (customer notification credit monitoring, forensics, hiring a law firm, etc.).
Security Wrongful Act
The security liability insuring agreement provides coverage for the Insured for allegations of a “Security Wrongful Act”, including:
• The inability of a third-party, who is authorized to do so, to gain access to the insured’s computer systems.
• The failure to prevent unauthorized access to or use of a computer system, and/or the failure to prevent false communications such as “phishing” that results in corruption, deletion of or damage to electronic data, theft of data and denial of service attacks against websites or computer systems of a third party.
• Protects against liability associated with the Insured’s failure to prevent transmission of malicious code from their computer system to a third party’s computer system.
Multimedia Liability
Provides coverage against allegations that include: Defamation, libel, slander, emotional distress, invasion of the right to privacy, copyright and other forms of intellectual property infringement (patent excluded) in the course of the Insured’s communication of media content in electronic (website, social media, etc.) or non-electronic forms Other “Cyber” insurance policies often limit this coverage to content posted to the Insured’s website. Our policy extends what types of media are covered as well as the formats where this information resides.
Cyber Extortion
Expense and payments to a harmful third party to avert potential damage threatened against the Insured such as the introduction of malicious code, system interruption, data corruption or destruction or dissemination of personal or confidential corporate information.
Business Income and Digital Asset Restoration
Provides for lost earnings and expenses incurred because of a security compromise that leads to the failure or disruption of a computer system, or, an authorized third-party’s inability to access a computer system.
Restoration costs to restore or recreate digital (not hardware) assets to their pre-loss state are provided for as well.
What’s more, the definition of Computer System is broadened to include not only systems under the insured’s direct control but also systems under the control of a service provider with whom the insured contracts to hold or process their digital assets.
PCI-DSS Assessment
The Payment Card Industry Data Security Standard (PCI-DSS) was established in 2006 through a collaboration of the major credit card brands as a means of bringing standardized security best practices for the secure processing of credit card transactions.
Merchants and service providers must adhere to certain goals and requirements in order to be “PCI Compliant,” and under specific agreements, may subject an insured to an “assessment” for breach of such terms. The BCS Cyber and Privacy Liability.
Cyber Deception
The Cyber Deception extension, if the applicant is eligible and if purchased for an additional premium, provides coverage for the intentional misleading of the Applicant by means of a dishonest misrepresentation of a material fact contained or conveyed within an electronic or telephonic communication(s) and which is relied upon by the Applicant believing it to be genuine. This is commonly known as “spear-phishing” or “social engineering”.
Claims What is the claims-handling process?
Companies have 24-hour data breach hotline available to report incidents or even suspected incidents.
As soon as you suspect a data breach incident or receive notice of a claim, you should call the hotline listed in your policy immediately.
The companies have designated legal firms that have been contracted to triage initial notices in this regard. This can be done by sending an email with a brief description of the incident, including your contact information, to the claims-reporting email address listed in your policy.
Contact us
This is a brief outline of Cyber Liability, how it works, and what this policy covers. Jim Lyons Insurance Agency has quick 5-minute quote & easiest issue for companies up to $100,000,000 in revenue for Cyber Liability. We will email sample policy with the quote. Email us for additional info or a quote at jlia@insurit.com.
Call us for a quick online quote 800-637-5088 email jlia@insurit.com
